Windows Installer custom actions, UAC and elevation
We had a problem this week where a merge module from a third party was causing our installer to fail under UAC.
The installation was being elevated, but the custom actions (which were doing things such as file system and registry operations) were still failing due to security exceptions.
The root cause was that the merge module contained custom actions that were still not being run under the elevated account.
The reason behind this is a common one when scheduling deferred actions; the custom action must have the Impersonate flag set to false.
You can do this in WiX code by setting Impersonate to No:
<CustomAction Id="RegisterAspNet4" BinaryKey="WixCA" DllEntry="CAQuietExec"
Execute="deferred" Return="check" Impersonate="no" />The documentation in WiX on the Impersonate attribute reads (emphasis mine):
This attribute specifies whether the Windows Installer, which executes as LocalSystem, should impersonate the user context of the installing user when executing this custom action. Typically the value should be ‘yes’, except when the custom action needs elevated privileges to apply changes to the machine.
Being a third party merge module, we had to fix this ourselves by opening up Orca and setting this flag manually.
You can do this by looking at the CustomAction table, finding your custom action in the list, and checking the Type field.
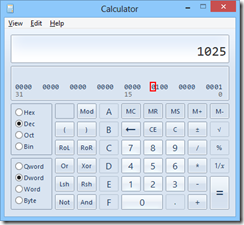
The Type field is a field full of flags, and will show up as a decimal number e.g. 1025.
If you open up Windows Calculator, switch to Programmer (View > Programmer or Alt+3), choose Decimal and enter the number, you can check the bit fields:
The first bit is set to signify it as an In-Script Execution custom action (type 1).
The 11th bit is set to signify Deferred execution (i.e. instead of running immediately, we schedule when the installer should run our custom action).
The 12th bit (the one I’ve highlighted) is the one that turns off impersonation; this is the bit we need to flip on to disable impersonation for this custom action, so that it runs with elevated privileges.
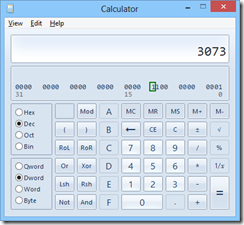
Being the twelfth bit, that is a value of 2048, so we can just add that to our value, giving us 3073:
You can see the No Impersonate bit is now flipped.
You can now update the value in Orca and save the merge module (or create a transform).